How to store aes encryption key images are available in this site. How to store aes encryption key are a topic that is being searched for and liked by netizens today. You can Download the How to store aes encryption key files here. Download all free photos and vectors.
If you’re looking for how to store aes encryption key images information related to the how to store aes encryption key keyword, you have pay a visit to the right site. Our website always gives you hints for seeking the maximum quality video and picture content, please kindly search and find more enlightening video articles and images that match your interests.
AES is used in SSL data session ie. Not all key generation methods are created equal and you may want to explicitly choose eg. This is especially of use for providers for security tokens. AES is a symmetric encryption. AES is used in SSL data session ie.
How To Store Aes Encryption Key. Thats why SSL certificate cant use AES but must be asymmetrical ones eg. Not all key generation methods are created equal and you may want to explicitly choose eg. SSL negotiation is basically to define AES key to be used by data session. AES Advanced Encryption Standard.
 Public Key Encryption Demo Comparison Between Pgp Vs Aes From adeptia.com
Public Key Encryption Demo Comparison Between Pgp Vs Aes From adeptia.com
Thats why SSL certificate cant use AES but must be asymmetrical ones eg. The derivation of the round keys looks a bit different. Not all key generation methods are created equal and you may want to explicitly choose eg. For an overview see disk encryption. AES is used in SSL data session ie. The key generation method of a provider.
Though AES is more secure than RSA in same bit size AES is symmetrical encryption.
For discussion of different software packages and hardware devices devoted to this problem see disk encryption software and disk encryption. To read simple AES encryption read linked post. For discussion of different software packages and hardware devices devoted to this problem see disk encryption software and disk encryption. This is especially of use for providers for security tokens. The key generation method of a provider. AES is used in SSL data session ie.
 Source: atpinc.com
Source: atpinc.com
AES-128 uses 10 rounds AES-192 uses 12 rounds and AES-256 uses 14 rounds. The key generation method of a provider. AES is used in SSL data session ie. Not all key generation methods are created equal and you may want to explicitly choose eg. SSL negotiation is basically to define AES key to be used by data session.
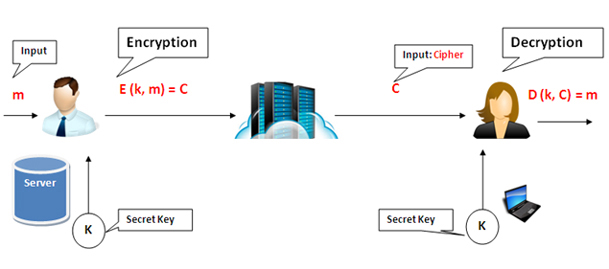 Source: codeproject.com
Source: codeproject.com
Though AES is more secure than RSA in same bit size AES is symmetrical encryption. AES is a symmetric encryption. For discussion of different software packages and hardware devices devoted to this problem see disk encryption software and disk encryption. Not all key generation methods are created equal and you may want to explicitly choose eg. To read simple AES encryption read linked post.
 Source: security.stackexchange.com
Source: security.stackexchange.com
Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device eg a hard disk. AES Advanced Encryption Standard. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. The derivation of the round keys looks a bit different. This is especially of use for providers for security tokens.
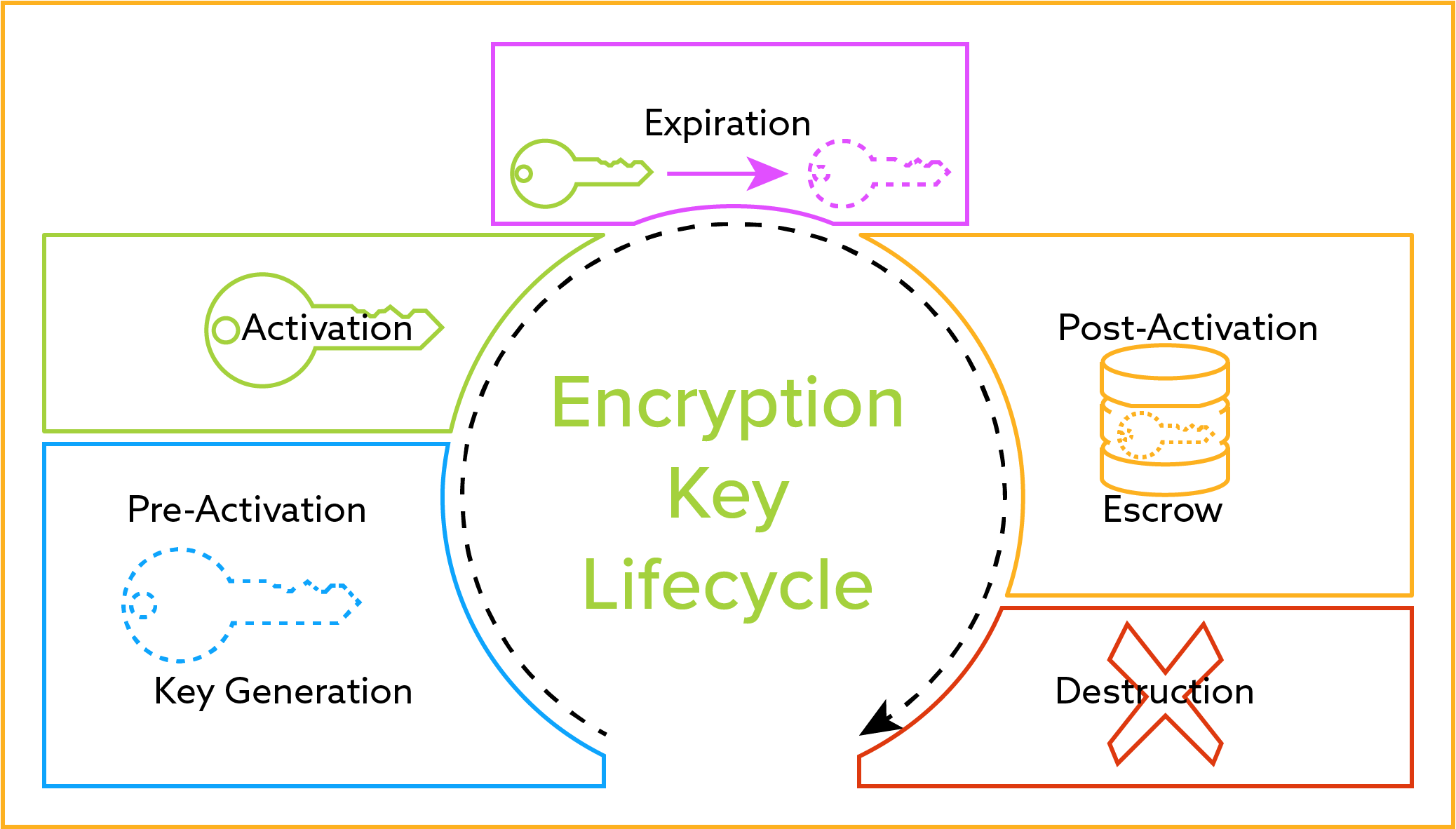 Source: info.townsendsecurity.com
Source: info.townsendsecurity.com
Thats why SSL certificate cant use AES but must be asymmetrical ones eg. To read simple AES encryption read linked post. The derivation of the round keys looks a bit different. This article presents cryptographic aspects of the problem. The longer key sizes use more rounds.

SSL negotiation is basically to define AES key to be used by data session. SSL negotiation is basically to define AES key to be used by data session. This article presents cryptographic aspects of the problem. Not all key generation methods are created equal and you may want to explicitly choose eg. For an overview see disk encryption.
 Source: aws.amazon.com
Source: aws.amazon.com
This is especially of use for providers for security tokens. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. SSL negotiation is basically to define AES key to be used by data session. The longer key sizes use more rounds. AES Advanced Encryption Standard.
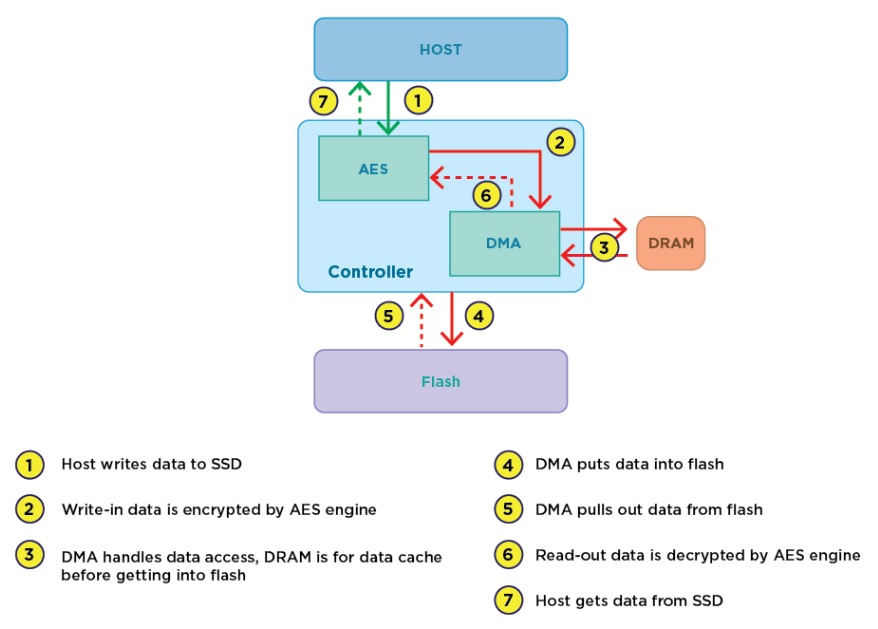 Source: transcend-info.com
Source: transcend-info.com
Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device eg a hard disk. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. AES is a symmetric encryption. Disk encryption is a special case of data at rest protection when the storage medium is a sector-addressable device eg a hard disk. For discussion of different software packages and hardware devices devoted to this problem see disk encryption software and disk encryption.
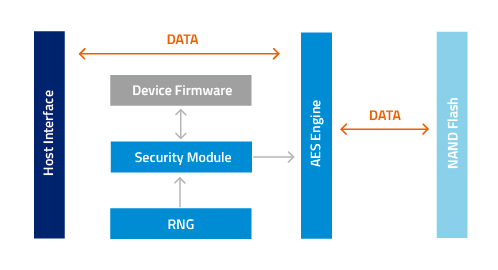 Source: atpinc.com
Source: atpinc.com
Learn to use Java AES 256 bit encryption to create secure passwords and decryption for password validation. AES is used in SSL data session ie. AES is a symmetric encryption. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. AES-128 uses 10 rounds AES-192 uses 12 rounds and AES-256 uses 14 rounds.
 Source: youtube.com
Source: youtube.com
Learn to use Java AES 256 bit encryption to create secure passwords and decryption for password validation. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. Not all key generation methods are created equal and you may want to explicitly choose eg. Thats why SSL certificate cant use AES but must be asymmetrical ones eg. AES-128 uses 10 rounds AES-192 uses 12 rounds and AES-256 uses 14 rounds.
 Source: maximintegrated.com
Source: maximintegrated.com
This article presents cryptographic aspects of the problem. AES Advanced Encryption Standard. This is especially of use for providers for security tokens. Learn to use Java AES 256 bit encryption to create secure passwords and decryption for password validation. For an overview see disk encryption.
 Source: mkyong.com
Source: mkyong.com
AES is a symmetric encryption. The derivation of the round keys looks a bit different. Though AES is more secure than RSA in same bit size AES is symmetrical encryption. Learn to use Java AES 256 bit encryption to create secure passwords and decryption for password validation. SSL negotiation is basically to define AES key to be used by data session.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to store aes encryption key by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






